Aircrack ng dll windows like
As long as you are only using aircrack-ng to pentest your own network, I will give you this advice. This advice is for an install on Ubuntu. I do not know how to do this on windows (special drivers, wifi cards, etc.). You will have to capture packets before you go out cracking the WEP or WPA. You can do this using a tool named tcpdump. Dump the packets into a file, and then run them through aircrack-ng. Make a Live USB of the Ubuntu operating system. Install aircrack-ng by typing into the terminal (which can be found by searching it in the dash menu /the little icon in the upper left corner : sudo apt-get install aircrack-ng. Further instructions here. My friend, if you do not absolutely have to do this, please stay away from it. From the computer knowledge that I assume you have, you should probably start-off doing something easier. DO NOT, UNDER ANY CIRCUMSTANCES, TRY TO CRACK THE WEP CODE OF SOMEONE ELSE' S WIFI CONNECTION. THIS IS NOT ONLY IMMORAL, IT' S ILLEGAL ( AGAINST THE LAW). YOU WILL FIND YOURSELF IN PRISON WITH ANY SUCH ATTEMPT. Good luck my friend.
Tutorila How to Packet injection Aireplay-ng Windows XP. Operating system Microsoft Windows XP SP2. Wireless card: CM9 ( WNC AR5213) + mini PCI/ PCI reduction. Aplictions: package Aircrack-ng-win 0.9. Driver: Comm View for Netgear + library (older commview.dll or new ca2k.dll). Read Metasploit Hacking Windows. Feel free ask for or post txt mistakes. ( All the software used in the tutorial it’s possible to download in the download DIR. Hardware the Linux version has been ported to the Zaurus and Maemo platforms, and a proof-of-concept port has been made to the i Phone. The Aircrack-ng software suite includes: airbase-ng: Multi-purpose tool aimed at attacking clients as apposed to the Access Point ( AP) itself. aircrack-ng: An 802.11 WEP and WPA/ WPA2- PSK key cracking program. airdecap-ng: Decrypt WEP/ WPA/ WPA2 capture files. airmon-ng: Enable monitor mode on wireless interfaces. airdecloak-ng: A tool that removes wep cloaking from a pcap file. airdrop-ng: A program used for targeted, rule-based deauthentication of users. airgraph-ng aireplay-ng: Used to inject frames. airodump-ng: Used for packet capturing of raw 802.11 frames and is particularly suitable for collecting WEP IVs for the intent of using them with aircrack-ng. airtun-ng: A virtual tunnel interface creator. airolib-ng: An aircrack-ng suite tool designed to store and manage essid and password lists, compute their Pairwise Master Keys ( PMKs) and use them in WPA/ WPA2 cracking. airserv-ng: A wireless card server which allows multiple wireless application.
Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are. In this first installment on password cracking, we'll assume the simplest arrangement; you're running Windows, attacking Windows, and have physical access to the computer whose passwords you're attempting to crack. In future installments, we'll look at cracking passwords remotely, with and on Linux operating systems, and cracking famous web applications such as Gmail and Facebook, so keep coming back! Step 1: Download Pwdump3 Windows systems encrypt user passwords and store them in a file named SAM and store them in the following directory:c:\ Windows\system32\config The first thing we need to do is grab this file. In an earlier article, we used Metasploit to hack into the malicious dictator's computer and grab his password hashes. We can also grab the hashes without Metasploit if we have physical access to a computer on the network. This can be done with a neat piece of software called pwdump3. It's installed on Back Track already, but you can download it for free on Windows using the link below. Click here to download pwdump3 for Windows. Pwdump3 is able to grab the encrypted passwords for us, and we can then crack them with another password cracking tool. So, let's grab that SAM file with pwdump3! Step 2: Grab the Hashes Open a command prompt. Now navigate to the folder where you placed your pwdump3 app. I put mine on the desktop. Now type: mycomputer hashdumpfile.txt When you hit enter, pwdump3 will grab the password hashes and place them in the file called hashdumpfile.txt. Make sure that you replace mycomputer in the command above with the actual name of your computer. If you don't know the name of.
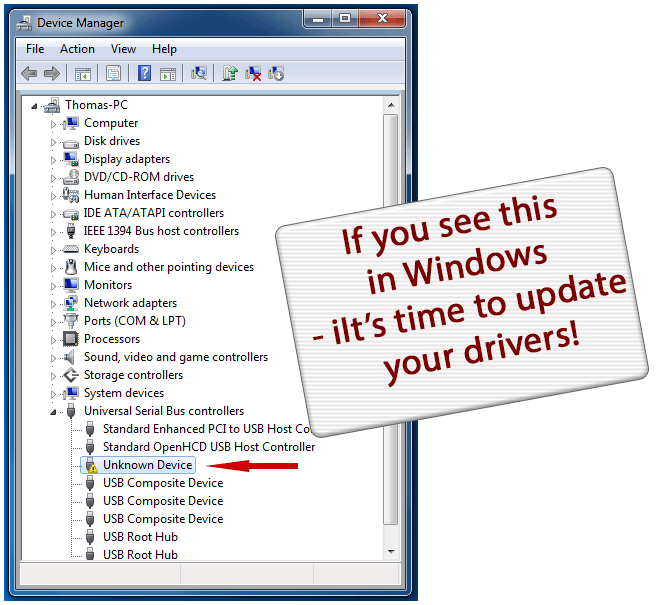
Hello Friends now I will show you how to install aircrack-ng in windows 8 /7 /xp step 1 you must download aircrack-ng for windows. you can download it in.
Introduction Aircrack-ng is an 802.11 WEP and WPA- PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like Kore K attacks, as well as the all-new PTW attack, thus making the attack much faster compared to other WEP cracking tools. In fact, Aircrack-ng is a set of tools for auditing wireless networks. What is Aircrack-ng? If you are impatient and want to know how to get started, jump to the Getting Started Tutorial. Aircrack-ng is the next generation of aircrack with lots of new features: More cards/drivers supported More OS and platforms supported WEP dictionary attack Fragmentation attack Improved cracking speed Capture with multiple cards Optimizations, other improvements and bug fixing Note: Check trac for planned and requested features News Commercial support survey We are going to also offer commercial support (besides other existing support options) and I'd like to ask you to take 5 minutes of your time to give your opinion in this survey if you're interested in. Do not hesitate to contact me if you have any question about it. Open WIPS-ng logo contest I launched a few months ago another project, Open WIPS-ng, an Open Source Wireless IPS. We need a logo and that's why there's a contest. The prize for the winner is 0. More details on the website. Updates I've seen a couple of post in the forum asking if the project was still alive since there was no update on the website. Yes it is still alive as you can see on trac and Twitter, I just haven't been updating the website. By the way, you should use the version from our subversion instead of the stable, lots of things have changed. For those on IRC, we finally got a cloak for the project. And it is not limited to the developpers of Aircrack-ng. So if you help others on a regular.
If you have forgotten the password that you use to connect to the Internet using a Wi- Fi connection, you can reset the router or use an application like Aircrack-ng to find it out. Although this isn't what most users use this application for. Aircrack-ng is part of a group of applications known as packet sniffers, this means, it's an application that intercepts and logs data streams that flow across a network. It will let the user recover the WEP and WPA- PSK key from any wireless connection based on the IEEE 802.11 standard. To manage this, it has a group of tools like airbase-ng, aircrack-ng, airodump-ng., each of these for a specific task. The method implemented by Aircrack-ng is called an FMS attack, receiving this name in honor of Fluhrer, Mantin and Shamir that were the first to demonstrate the weakness of WEP ciphering. Furthermore, it includes improvements made to Kore K and others. To find out the passwords of wireless networks that aren't properly protected, Aircrack-ng captures the first packages that are transmitted by a connection, allowing the user to obtain the passwords and use them to connect to the Internet. The use of Aircrack-ng requires advanced network knowledge. Requirements and additional information: Requires the users to create their own DLLs to connect the application with the wireless card. Antony Peel at Google +.

